Build the most secure facilities
Install Trout's Cyberbox in your physical sites to get asset visibility, add layers of protection and accelerate compliance.
CONTEXT-AWARE CYBERSECURITY
Smart, Plug & Play Cybersecurity
Trout Core Engine allows to quickly deploy cybersecurity controls in a given environments, layering expert detections and frameworks on top of your business context.
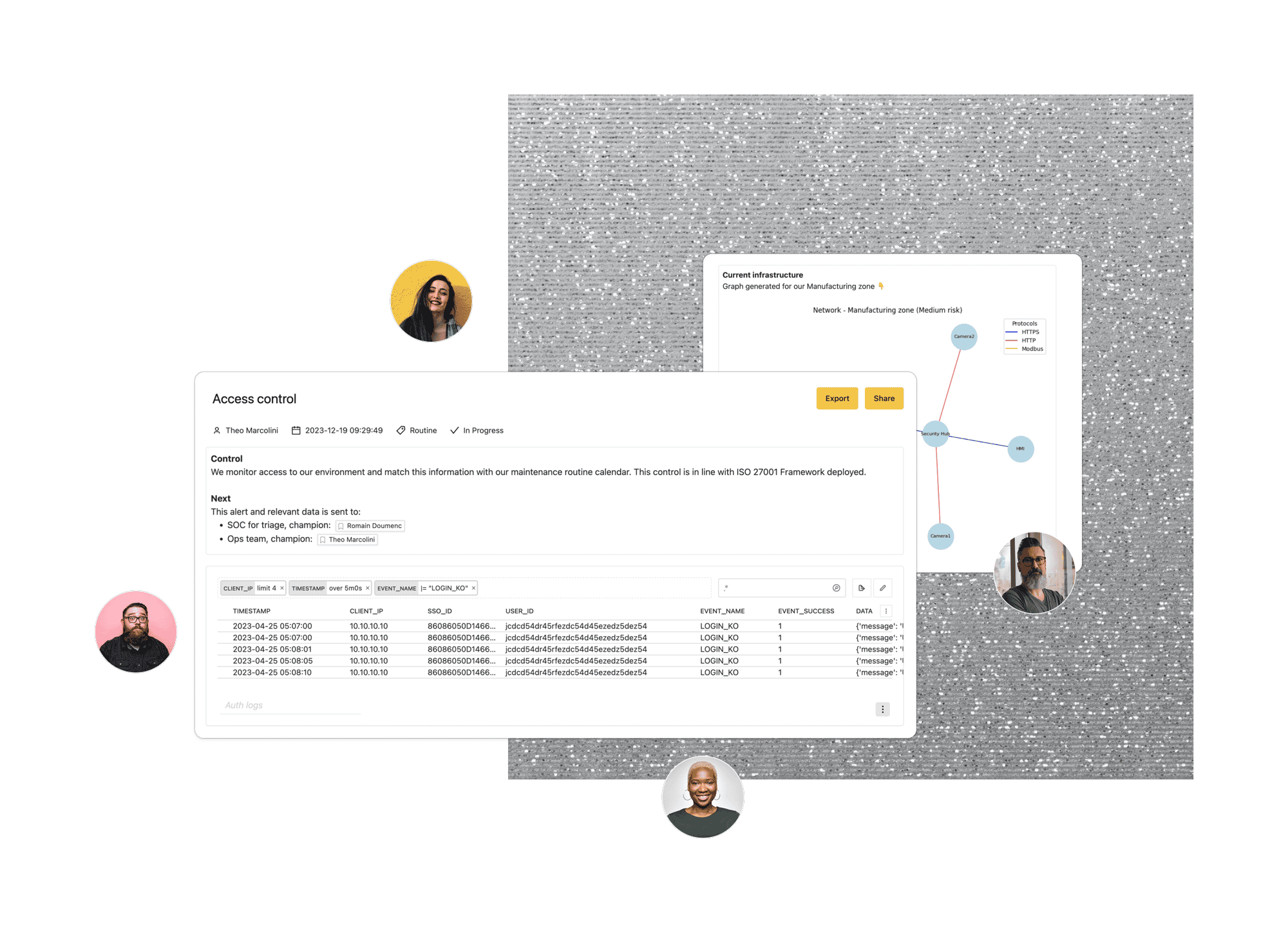
Trout Core Engine merges near-native performance with high-level context

Execution Speed
Low-level architecture that's optimized for just-in-time parsing and efficient execution, effectively breaking through performance barrier of traditional processing pipelines.

Security
A sandboxed environment, providing a layer of security against malicious actions. Trout Core Engine uses Memory Safety, Control-Flow Integrity and Clang/LLVM CFI compiler infrastructure to ensure high-level of security.

Correlation
Trout Core Engine treats data as a raw object to be handled in the runtime. A key benefit of this convention is the one-for-one in/out byte stream design, providing correlation capabilities at the edge.

Intuitive design
Trout is the maintainer of the open-source project Rx, a reactive rendering engine using WASM, providing rich-dynamic frontend for data manipulation.
Plug & Play Solutions tailored for your environments
-
Industrial Sites
-
On-Premise Applications
-
Supply Chain Security
-
Log Pipeline
Cyberbox for Industrial Environments
An elegant solution to secure your factory and production sites. Trout OT is a plug and play hardware to discover and manage assets, enhance network security without rewiring and reduce the amount of paperwork required for compliance.
Sidecar Agent for On-Premise
Install Trout AppSec binary in your on-premise environments, and leverage Trout Core Engine to accelerate your app security and compliance reviews.
Deploy Cyberboxes across your Supply Chain
Collaborate with your partners to create a vertical visibility on your supply chains through Trout plug & play Cyberbox.
Log Skimming Pipeline
Plug & Play Log Skimming Pipeline to process logs from applications and systems, and skim output to your SIEM or log sink.
Integrate new environments in your existing processes
Trout Plug & Play solutions are aimed to interact with your existing tools and processes. Our solutions allow the processing of logs via Trout Core Engine, and to skim the relevant information to your existing solutions.
Increase visibility, and compliance controls, while keeping the noise down.



.png?width=429&height=117&name=images%20(1).png)




.png?width=388&height=130&name=images%20(2).png)
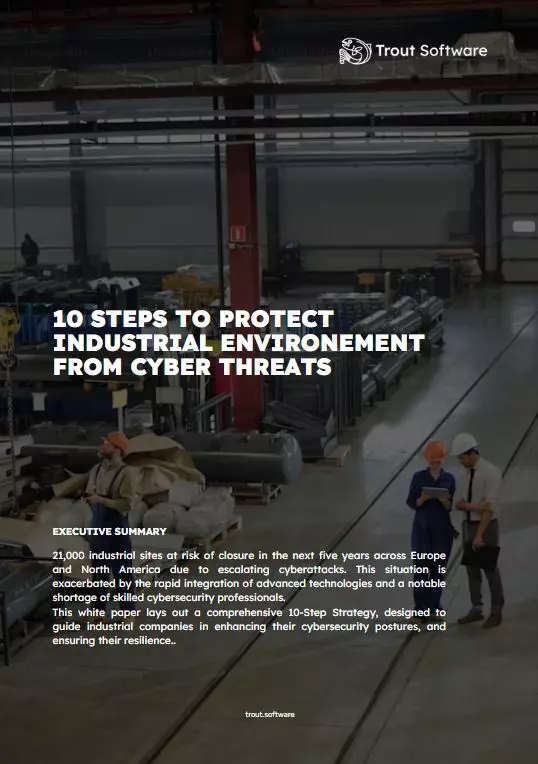
10 Steps to Protect Industrial Environments from Cyber Threats
A comprehensive 10-Step Strategy designed to strengthen the cybersecurity defenses and resilience of industrial companies.