Introduction
After more than 9 years without changes in the ISO 27001 standard, in October 2022, changes have been published. These changes are intended to correspond more with the informatic world of today which has largely evolved since 2013, the year of the last changes. The majority of the changes made in the standard are in the area of controls, in particular the addition of 11 new controls in Annex A.
5.7 Threat Intelligence
Description of the control :
According to Gartner, threat intelligence is : “Evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject's response to that menace or hazard”
Expectations from the standard :
“Information relating to information security threats should be collected and analysed to produce threat intelligence”
Purpose :
This control is to ensure that the organization has a process in place for monitoring and analyzing information about potential or actual security threats, vulnerabilities, and incidents. This aims to help organizations take a proactive approach to managing security risks by providing timely and relevant information to support decision-making and incident response.
Attributes :
.jpg?width=1461&height=426&name=5.7%20Threat%20intelligence%20%20(1).jpg)
5.23 Information security for use of cloud services
Description of the control :
Expectations from the standard :
“Processes for acquisition, use, management and exit from cloud services should be established in accordance with the organisation’s information security requirements.”
Purpose :
The 5.23 control aims to ensure that an organization's use of cloud services does not pose a risk to the confidentiality, integrity, and availability of its information.
This control is designed to help organizations manage the security risks associated with cloud services by implementing and maintaining appropriate security measures at every stage of the service lifecycle.
To control the risk of using cloud services, the company can, for example, issue a specific policy to all stakeholders in the company.
Attributs :
.jpg?width=1463&height=385&name=5.23%20Information%20security%20for%20use%20of%20cloud%20services%20(1).jpg)
5.30 ICT readiness for business continuity
According to Technopedia, ICT is : “Information and Communications Technology (ICT) is the convergence of computing, telecommunication and governance policies for how information should be accessed, secured, processed, transmitted and stored.”
Description of the control :
Expectations from the standard :
“ICT readiness should be planned, implemented, maintained, and tested based on business continuity objectives and ICT continuity requirements.”
Purpose :
The objective of monitoring is to ensure that an organization's information and communication technology (ICT) systems will be available in the event of a disruption or crisis. The goal is therefore to assess whether the integrity of information is maintained before, during and after a period of disruption.
Attributs :
.jpg?width=1471&height=431&name=5.30%20ICT%20readiness%20for%20business%20continuity%20(1).jpg)
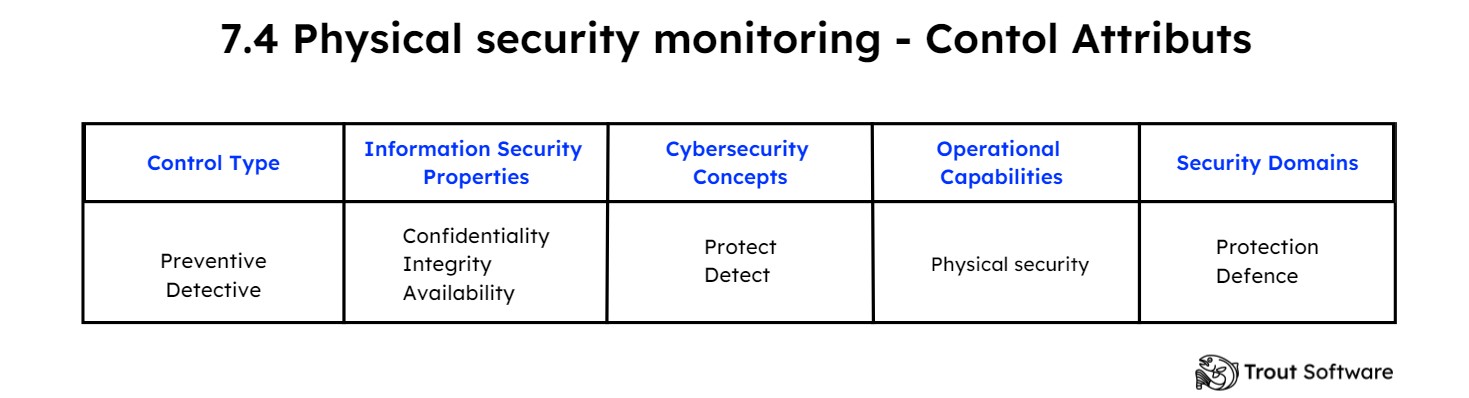
7.4 Physical security monitoring
Description of the control :
Expectations from the standard :
“Premises should be continuously monitored for unauthorised physical access.”
Purpose :
The purpose of this control is to have continuous monitoring of physical security measures within an organization to ensure the protection of physical assets and people. Companies must therefore detect any intrusions into physical spaces with limited access. The surveillance of these areas can be done via cameras, intrusion detection systems, security personnel...
Attributs :
8.9 Configuration management
Description of the control :
Expectations from the standard :
“Configurations, including security configurations, of hardware, software, services and networks should be established, documented, implemented, monitored and reviewed.”
Purpose : Companies are evolving in an increasingly digitalized, API driven world, where the adoption of a new tool can take a few seconds. In this context, the main goal of this control is to avoid configuration drifts. To do this, companies must implement a system that allows them to effectively manage and control the configuration of their information systems and IT infrastructure.
The company should then establish standardized processes for configuration identification, control, status accounting, and auditing.
Attributs :
.jpg?width=1475&height=430&name=8.9%20Configuration%20management%20(1).jpg)
8.10 Information deletion
Description of the control :
Expectations from the standard :
“Information stored in information systems, devices or in any other storage media should be deleted when no longer required.”
Purpose :
The purpose of this control is to delete any information belonging to the company but which is no longer useful for these activities.
We often talk about data minimization, which allows companies to manage a smaller amount of data and thus in case of data leakage to minimize the risks.
This control will therefore require the company to define a time period for each piece of data after which it can be deleted because it will no longer be useful for the business.
Attributes :
.jpg?width=1472&height=408&name=8.10%20Information%20Deletion%20(1).jpg)
8.11 Data masking
Description of the control :
Expectations from the standard :
“Data masking should be used in accordance with the organisation’s topic-specific policy on access control and other related topic-specific policies, and business requirements, taking applicable legislation into consideration.”
Purpose :
Data masking is the action of protecting sensitive data, especially PPII data or financial data, by obfuscating or replacing it with fictional or modified data while maintaining its usability for testing, development, or other non-production purposes.
The final purpose is to ensure the confidentiality and privacy of sensitive information when it is shared or used in environments where the full data is not required or should not be exposed.
Attributs :
.jpg?width=1467&height=426&name=8.11%20Data%20Masking%20(1).jpg)
8.12 Data leakage prevention
Description of the control :
Expectations from the standard :
“Data leakage prevention measures should be applied to systems, networks and any other devices that process, store or transmit sensitive information.”
Purpose :
The purpose of data leakage prevention is to protect valuable data assets, maintain data privacy, and prevent the potential financial, legal, and reputational consequences of data breaches or unauthorized data disclosures.
In order to protect itself, a company must conduct a risk assessment of this data, then define data security policies according to the risks identified.
Depending on the type of data, the criticality of the data, different measures can be implemented such as robust file permissions or restrict a user's ability to copy paste data.
It is also important to thoroughly monitor applications like Notion in which employees communicate and store a lot of information.
Attributes :
.jpg?width=1470&height=384&name=8.12%20Data%20Leakage%20Prevention%20(1).jpg)
8.16 Monitoring activities
Description of the control :
Expectations from the standard :
“Networks, systems and applications should be monitored for anomalous behaviour and appropriate actions taken to evaluate potential information security incidents.”
Purpose :
This control focuses on establishing a comprehensive monitoring system to track and analyze various activities within an organization's information systems and networks.
The goal is for the company to take a proactive stance on detecting and responding to security incidents, unauthorized access attempts, policy violations, and other abnormal or suspicious activities that may pose a risk to the organization's information assets.
The company can equip itself with a monitoring system to accomplish this control, the goal will be to define a baseline of normal behavior and monitor against the baseline.
Attributes :
.jpg?width=1474&height=442&name=8.16%20Monitoring%20Activities%20(1).jpg)
8.23 Web filtering
Description of the control :
Expectations from the standard :
“Access to external websites should be managed to reduce exposure to malicious content.”
Purpose :
The purpose of this control is to establish a list of Internet sites that are considered dangerous to consult, to list them, and then with the help of a web filtering tool to block employee access to these sites. It is also possible to block content by keywords or themes.
Web filtering is mainly performed to protect the company from sites or links that could cause malware infection.
It can also allow a company to block access to its employees to storage spaces or applications not authorized by the company and which can create shadow data.
Attributs :
.jpg?width=1470&height=390&name=8.23%20Web%20filtering%20(1).jpg)
8.28 Secure coding
Description of the control :
Expectations from the standard :
“Secure coding principles should be applied to software development.”
Purpose :
The purpose of this control is to minimize the vulnerabilities that can be created by a software code and thus to ensure its maximum security.
To do this, the company must ensure that it has a secure development environment that is built on secure and reliable infrastructure using secure software, services and providers.
In general, the company should respect the secure coding principles such as : input validation, output encoding, authentification and access control, secure data storage, regular security testing…
Attributs :
.jpg?width=1470&height=433&name=8.28%20Secure%20Coding%20(1).jpg)
How to automatise your ISO 27001 controls with Trout Software ?
Ready to deploy controls templates
Trout Software has developed a set of templates that allow you to quickly set up controls within your organization.
All our templates are completely customizable according to the company's wishes. To use these templates, simply follow the instructions provided by Trout Software and connect your data using the pre-built connectors in our software. Once the control is set up, you can automate it and then return to the library to choose the next control you wish to set up.
Compliance automation
In order to save you hours of manual tasks to verify the implementation and the results of the implemented controls, Trout Software allows you to automate these controls.
To do this, it is very simple, you just have to choose the control you want to automate, previously configure it with our template or by yourself, then automate it in our scheduler.
Once your control is chosen in our scheduler, you will have to configure the parameters of the control: date of the first control, number of repetitions and time between repetitions and then click on Schedule.
Real-time monitoring
Thanks to our innovative platform, you have access to a personalized control center for all your ISO 27001 controls and see their results in real time.
Indeed, on your control center in the Scheduler tab that you can see below, each control will return a green or red bar depending on the response of the positive or negative control to the rule.
This allows you to perform 24/7 monitoring and implement fast and optimized corrective actions.