Build the most secure & connected facilities
Connectivity is a pillar of Industrial performance.
Trout provides a hardware to accelerate secure connectivity through the implementation of
Demilitarized LAN
OVERLAY DEMILITARIZED LAN
Network performance and security
Trout Cyberbox provides a simple and scalable hardware to implement an Overlay Demilitarized LAN (OD LAN) across your industrial sites. Leverage the security of Demilitarized LAN, and the agility of an Overlay.
Thales secures environments with Trout
Thales, a top-tier defense company ranking among Europe's elite, has long been recognized for its steadfast commitment to security and technological innovation. In a strategic move to accelerate security by the edges, Thales embarked on a transformative initiative by integrating Trout into its ecosystem.

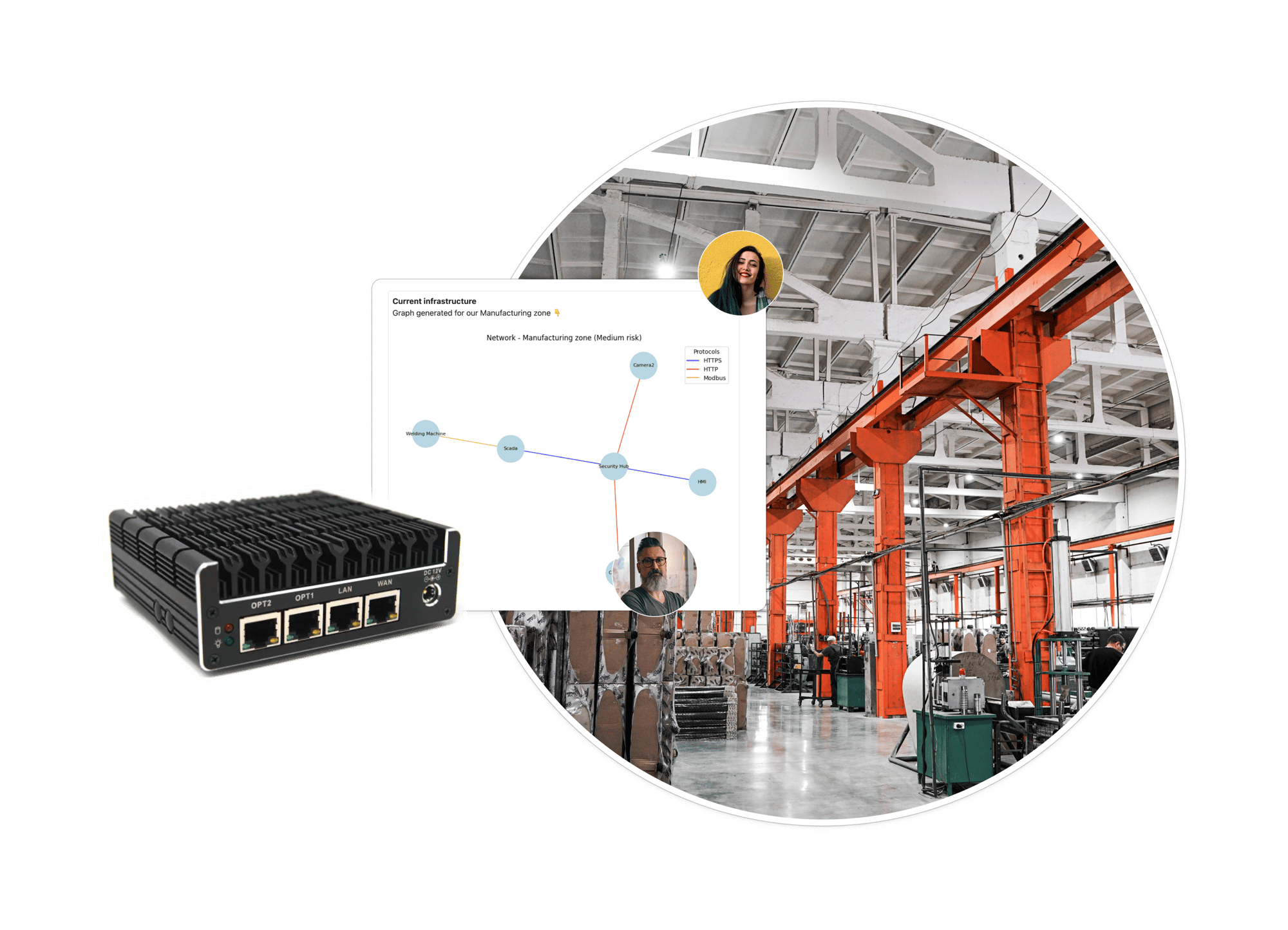
Trout Cyberbox
Build the most secure facilities. Trout proprietary hardware provides an integrated solution to scale DLANs across your infrastructure - gain visibility into your assets, deploy layers of protection, accelerate compliance. Offering transparent and dependable solutions to safeguard critical infrastructure.
Visibility
Out-of-the box asset discovery and management capacities, allowing you to detect existing assets in your environments and asset changes in real-time.
Protection
Trout Cyberbox runs native, scalable proxy - spanning across protocols - to accelerate the implementation of layers of protection and buffer zones.
Detections
Pre-built expert detections and frameworks in line with global regulations (NIS2, NIST, CMMC). With the ability to extend custom multi-system detections.Integration
Integrated log forwarder with Gb/s throughput, with skimming capacities and integration to log sink and SIEM products.
Compliance
Simplifying compliance management for information security regulations with edge proof collection and correlation with policies.
Accelerate and secure your industrial sites
At Trout, we work to help our customers deliver agile and secure networks, and to be able to tackle their digitalization efforts, from a strength position
10 Steps to Protect Industrial Environments from Cyber Threats
A comprehensive 10-Step Strategy designed to strengthen the cybersecurity defenses and resilience of industrial companies.