Modernize Industrial & Critical Networks
The Challenge
Traditional Scanning Breaks OT Environments
Active scanning assumes hosts can be probed, but OT devices rarely fit that assumption:
Many PLCs, controllers, and HMIs don’t respond well to probes
Vulnerability scanners generate traffic that can disrupt production
Agents can’t be installed on legacy or unpatchable equipment
Teams lack real visibility into what’s really on the network
The result? Inventories that are incomplete, inaccurate, or dangerous to collect.
Trout Secure Twin
Passive Asset Discovery from Natural Network Telemetry
By ingesting NetFlow and other passive telemetry from your existing network infrastructure, Trout builds:
Accurate device inventories
Protocol and port usage maps
Communication behavior baselines
Incremental asset and flow discovery over time
This approach is safe for legacy OT, doesn’t require agents, and imposes zero scanning noise on production systems.
Benefits at a Glance
Safe, Accurate OT Visibility — No Intrusion Required
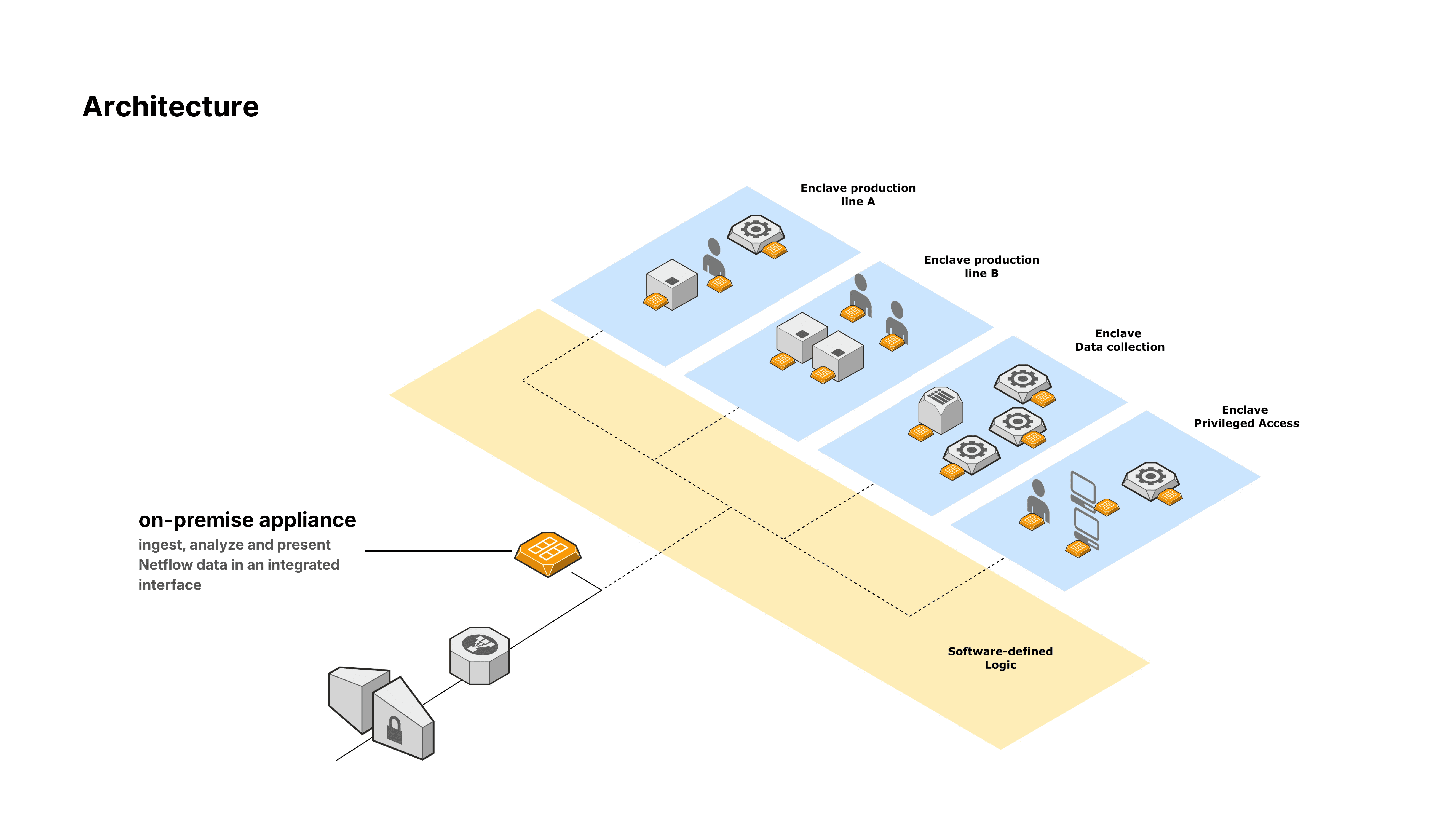
Trout Access Gate is an on-premise, plug-and-play appliance that brings modern networks to your factory & critical infrastructure, without disrupting production or rebuilding your network.

Production-Friendly
Designed for environments where uptime is mission-critical. Legacy assets stay untouched.

No Scanning
No active probes. No broadcast storms. No fragile devices distressed by network noise.

Automatic
Trout observes real traffic and updates the inventory in a click of a button.

Granular Context
Assets, protocols, services, enclaves and compliance assessment, integrated.

Foundation for Control
With accurate inventories in hand, teams can confidently build segmentation, access control, and Zero Trust policies.
How It Works
Passive Discovery in 5 Simple Steps
Enable a Monitoring Port: In the Trout interface, activate a dedicated monitoring port on the Access Gate.
Ingest NetFlow from the Network: Connect that port to NetFlow exported by an existing switch, router, or firewall.
Observe Natural Traffic: As real OT traffic flows (historian updates, HMI polling, OEM sessions) Trout watches and learns.
Automatically Identify Devices: Based on observed flows, Trout detects devices, protocols, services, communication patterns.
Build & Enrich Inventory: With a single click, confirmed assets enter your inventory. Over time, Trout continually refines and expands the view.
Who this is for
Why Passive Matters for OT
Most industrial equipment simply can’t endure the traffic patterns generated by standard network scanners.
With Trout’s passive method:
Legacy PLCs and HMIs are unaffected
Windows XP / Windows 7 systems stay stable
Sensitive control loops remain undisturbed
Inventories reflect real-world behavior, not scan assumptions
This visibility becomes the foundation for everything from segmentation planning to compliance reporting and risk assessments.
FAQ
Passive Network Visibility & Asset Inventory
Related Resources

Routed vs Switched Networks
Optimize industrial network security with insights on routed vs. switched networks.

Best Practices for Designing a Secure ICS Network
segmentation, access control, protocol management, and monitoring to protect critical infrastructure.
Beyond Purdue
A practical roadmap for securing modern industrial networks — without costly rebuilds.
In Summary - Passive Network Visibility & Asset Inventory Without Disruption.
Industrial networks rely on equipment that can’t tolerate active scanning, yet security and compliance require a clear picture of every asset and how it communicates. Trout solves this with passive network visibility: a safe, non-intrusive way to discover OT devices using the telemetry your network already produces.
By ingesting NetFlow from existing routers or switches, the Trout Access Gate automatically identifies devices, protocols, and communication patterns without touching the equipment or altering the network. The result is an accurate, continuously updated OT asset inventory and communication map, built entirely from real operational behavior.
This passive approach keeps production stable, supports legacy systems, and provides the foundation for segmentation and Zero Trust in industrial environments. No scanning, no agents, no downtime — just clean, reliable visibility into your OT landscape.