Trout Access Gate gives you the visibility, access control, and reporting that NIS2 requires.
You do not need to install agents on any devices.
Plug it in once to see your assets, manage connections, track activity, and collect audit evidence.
Asset Discovery & Inventory
Automatically identify every device — PLCs, HMIs, servers, IoT and unmanaged systems.
Identity-Based Access Enforcement
Controls who and what can reach sensitive assets, with role-based approval.
Micro-segmentation
Creates isolated enclaves for production systems to limit lateral movement.
Continuous Monitoring & Traffic Inspection
Real-time network monitoring for anomalies, threats, and policy violations.
Automated Logging & Reporting
Centralizes audit trails and generates compliance-ready reports.
The latest Access Gate update adds live traffic visibility, secure links between sites, and an enhanced risk assessment tool.
Skip the slow upgrades. Bring your sites up to a modern, dynamic security and compliance level in one move.
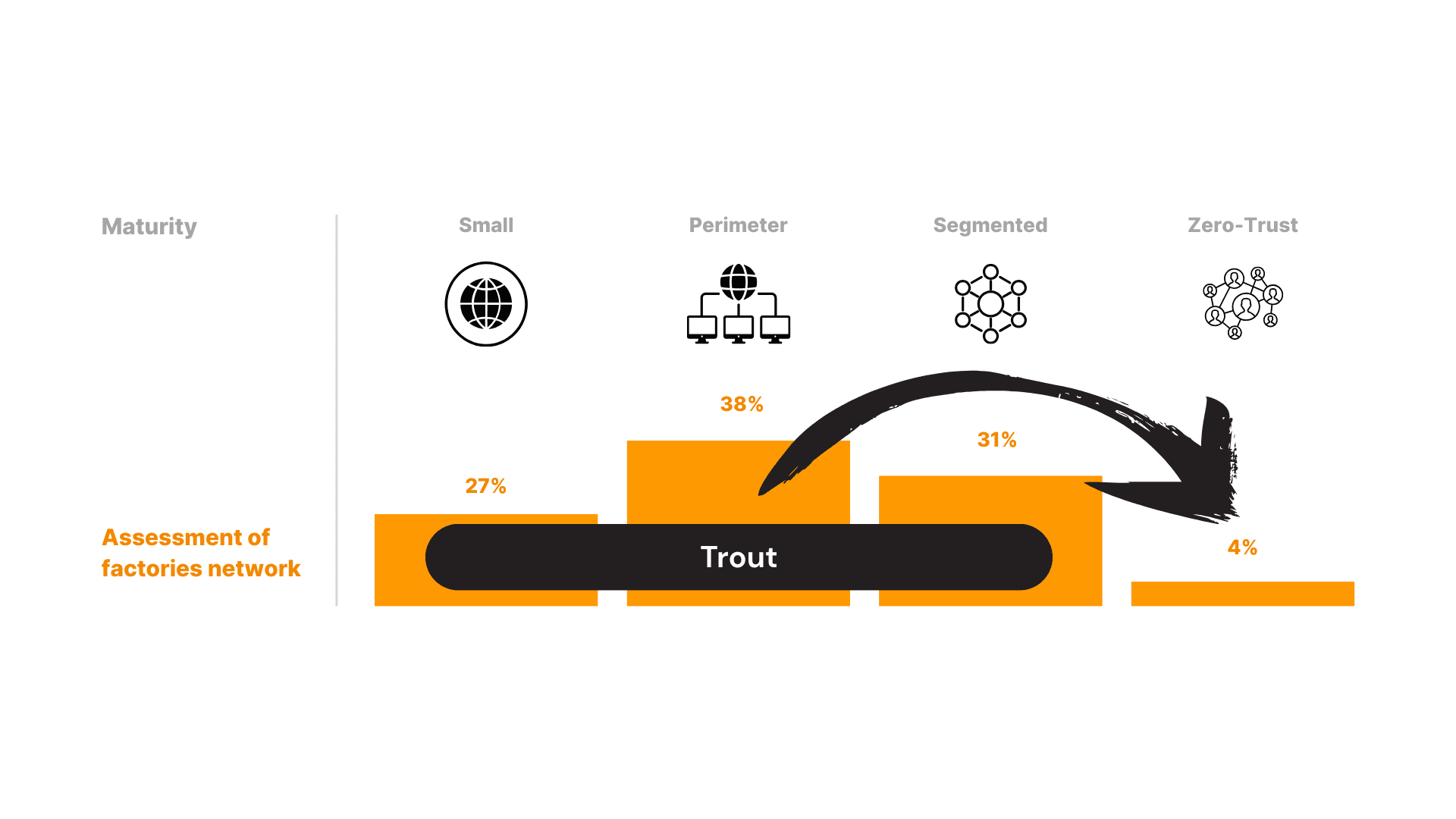
Summary of Trout Access Gate and NIS2 Coverage
Trout Access Gate helps organizations meet NIS2 requirements by securing access to on-premise systems without changing existing networks.
It automatically discovers assets, controls who can reach critical systems, segments environments to limit incidents and captures complete audit logs for compliance.
Trout supports most technical measures expected by NIS2 and can integrate with vulnerability scanners to close the one remaining requirement.
It works with or can replace firewalls and VPNs, provides secure internal and remote access and reduces the risk of ransomware or misuse across mixed IT, OT and IoT environments.
Deployment is fast, agentless and suitable for any NIS2 regulated organization, from public sector facilities to industrial sites and critical suppliers.
Specialized use cases
Zero-Trust security to protect IT/OT/IoT & Legacy Industrial Systems. Delivered as a plug-and-play appliance, no agents and no operational downtime.
Use Cases for Trout technology